Cybercrime , Fraud Management & Cybercrime , Ransomware
Alarming Trend: More Ransomware Gangs Exfiltrating Data
Criminals Increasingly Leak Stolen Data to Force Bitcoin Payoff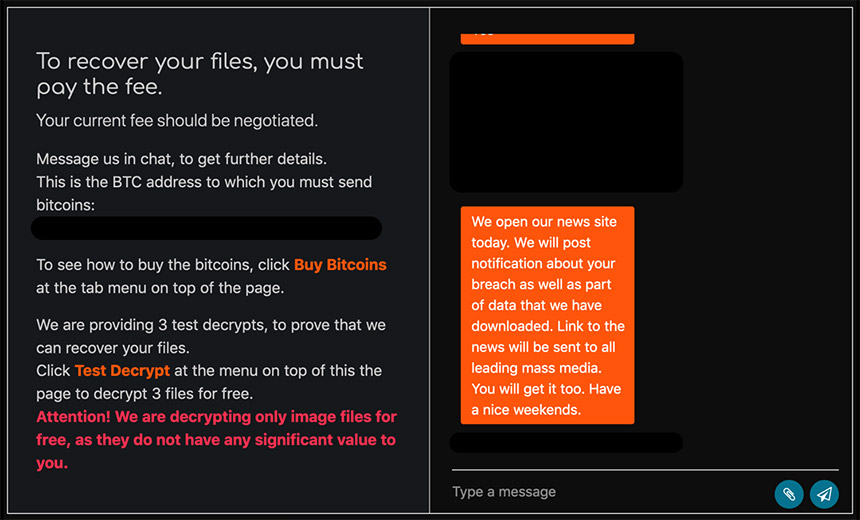
As if ransomware wasn't already bad enough, more ransomware gangs are now exfiltrating data from victims before leaving systems crypto-locked. Seeking greater leverage to force victims to accede to their ransom demand, attackers are threatening to leak stolen data and then following through. First, they leak chunks of data before leaking much more - or everything they took - in an attempt to teach future victims a lesson.
This "new, worrying trend" in ransomware - as Raj Samani, chief scientist at McAfee, calls it - has arisen quickly. It means that besides dealing with a ransomware attack, victims must also contend with a data breach, including their legal notification obligations.
In the past, many ransomware gangs claimed to have exfiltrated data from victims and threatened to leak it unless their demands were met. But it was typically an empty threat. Even if attackers did steal data, security experts say they typically preferred to sell any valuable information on cybercrime marketplaces or to put it to use themselves.
"Prior to the fourth quarter of 2019, data exfiltration extortion events were not nearly as prevalent as ransomware," says Coveware, a ransomware incident response firm, in a blog post. "We estimate that less than 5 percent of enterprise cyber extortion incidents involved data exfiltration and it was extremely rare to see the two methods of extortion combined."
Maze Leads the Way
In late October 2019, however, the Maze ransomware gang dumped almost 700 MB of data that it had stolen from Allied Universal, a California-based security services firm. And in December 2019, Maze created a dedicated website listing victims that had yet to pay, to which it began posting excerpts of stolen data (see: Maze Ransomware Gang Dumps Purported Victim List).
Earlier this month, one Maze victim - wire manufacturer Southwire - obtained a court order in Ireland to knock offline Maze's site, then hosted by an Irish hosting provider (see: Maze Ransomware Victim Sues Anonymous Attackers).
The attackers, who say they demanded a $6 million ransom payable in bitcoins, responded by relaunching their name-and-shame site, this time hosted by Chinese firms Alibaba and Tencent. On the XSS Russian cybercrime forum - formerly known as DamageLab - the gang also dumped 10 percent of the 14.1 GB of data it claims to have stolen from Southwire, saying that "until they agree to negotiate" the gang would leak 10 percent more each week. "Use this information in any nefarious ways that you want," the gang said.
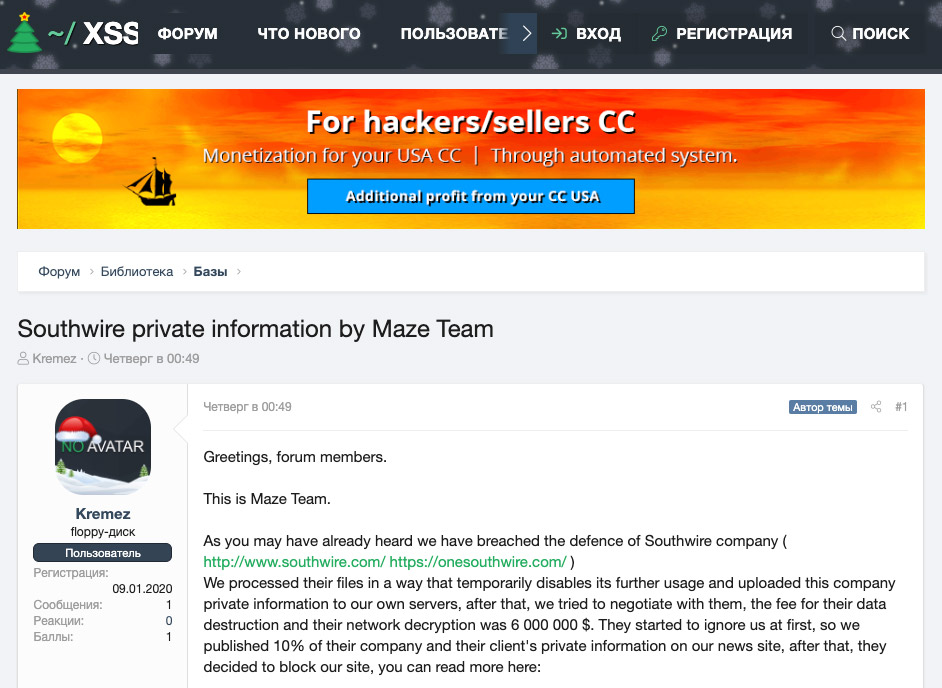
On its relaunched website, Maze has continued to list victims and dump data. "If you look at Maze’s website, you’ll see it lists a law firm in Houston, a medical testing lab in New Jersey and an accountancy firm with a couple of locations in New York," Brett Callow, a threat analyst at security firm Emsisoft, tells Information Security Media Group. "As far as I can tell, none of these companies have made a public disclosure, so people will not be aware that their data may have been exposed."
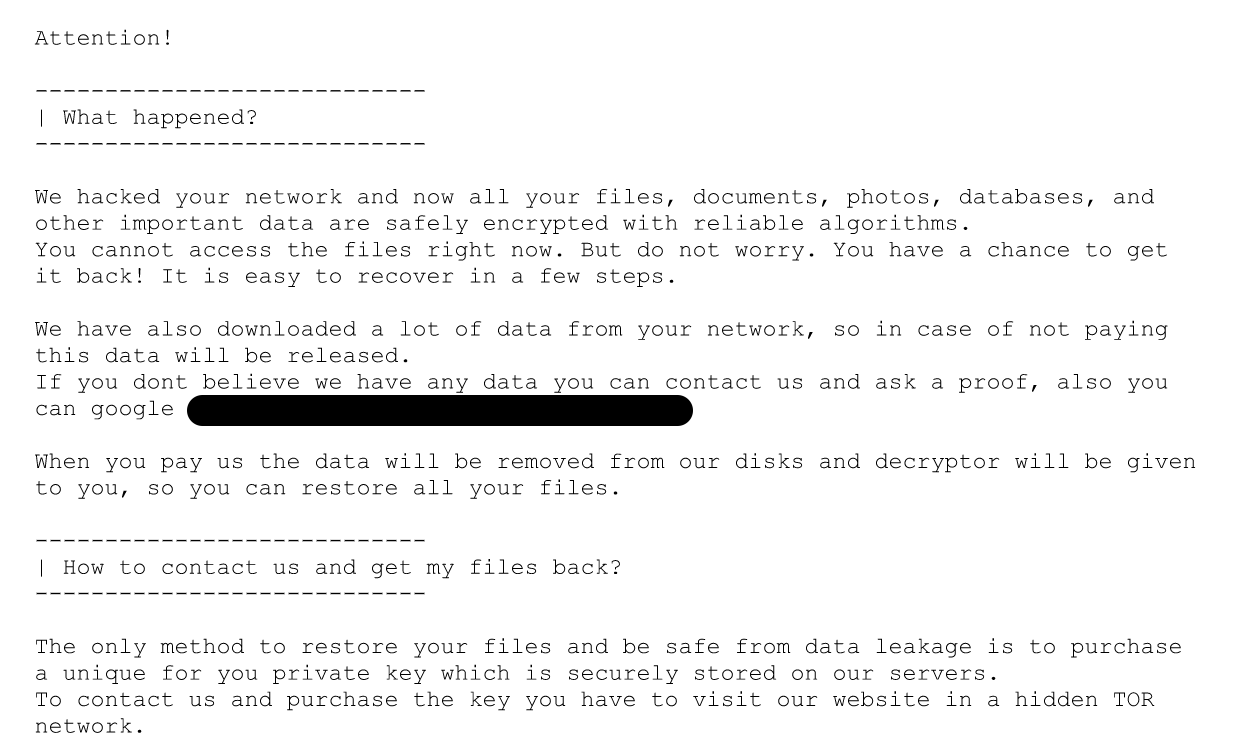
Sodinokibi and Nemty Follow
Last month, the operators of Sodinokibi - aka REvil and Sodin - said they would follow Maze's example and help affiliates leak exfiltrated data from victims that refused to pay.
"That’s the beauty of the ransomware-as-a-service model, where threat actors can outsource components of the attack that they may not be strong at," Samani says. "We have seen affiliates outsource the RDP stressing [aka brute-forcing] and indeed this approach will only continue as actors look for more ways to prompt payment" (see: Ransomware Gangs' Not-So-Secret Attack Vector: RDP Exploits).
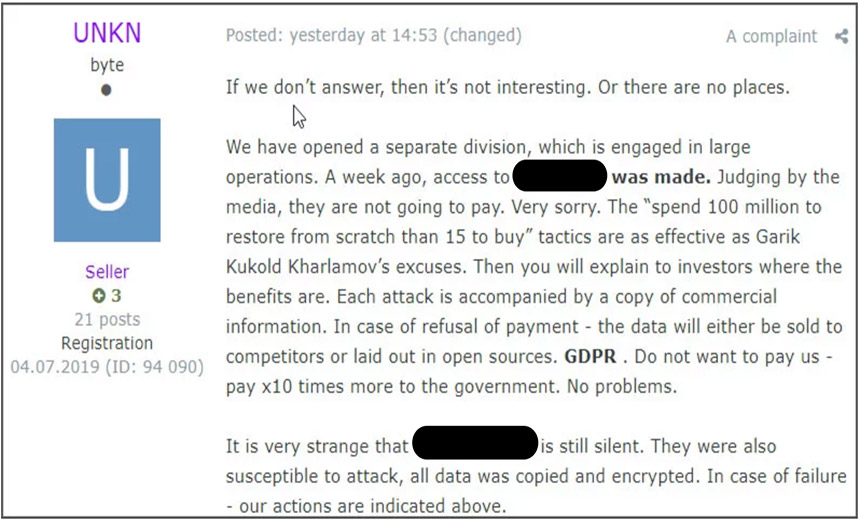
Coveware last week reported that it had "validated that Sodinokibi affiliates are exfiltrating data as part of their attacks" but not yet seen any data being dumped.
But that apparently came to pass this week. Bleeping Computer reports that a Sodinokibi affiliate has publicly leaked data that it claims to have stolen from New Jersey-based Artech Information Systems, described on its website as being "a minority- and women-owned diversity supplier and one of the largest IT staffing companies in the U.S."
After Maze and Sodinokibi, the developers of Nemty ransomware are now promising affiliates that their administrator portal will soon give them functionality for leaking non-paying victims' data to a dedicated website, Bleeping Computer reports.
Exfiltrated Data Used to Blackmail Individuals
Some gangs are also using stolen data to target not just organizations but individuals.
Dr. Richard E. Davis, who heads The Center for Facial Restoration - TCFFR - in Miramar, Florida, last week posted a notice to his practice's website saying that in early November 2019, attackers infected a server with ransomware and then demanded a ransom to not leak the personally identifiable information.
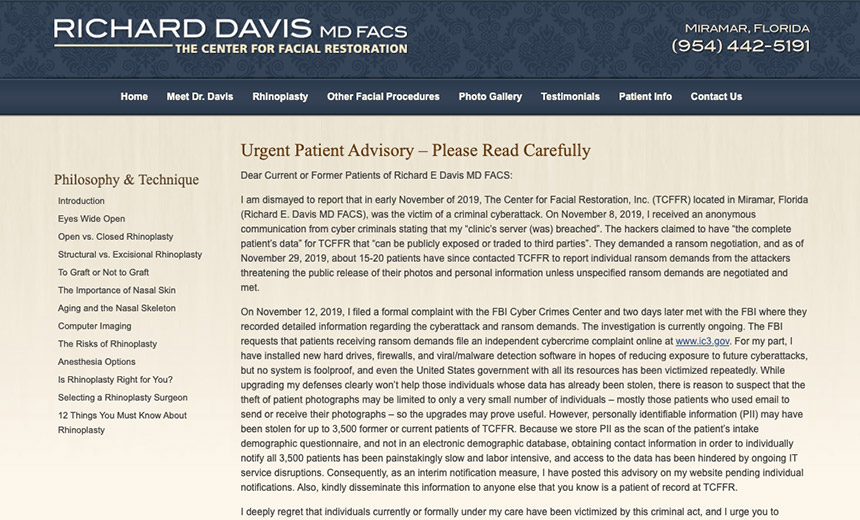
"On Nov. 8, 2019, I received an anonymous communication from cybercriminals stating that my 'clinic’s server (was) breached.' The hackers claimed to have 'the complete patient’s data' for TCFFR that 'can be publicly exposed or traded to third parties,'" Davis writes. "They demanded a ransom negotiation, and as of Nov. 29, 2019, about 15 to 20 patients have since contacted TCFFR to report individual ransom demands from the attackers threatening the public release of their photos and personal information unless unspecified ransom demands are negotiated and met."
Shaming May Backfire
Security experts say the jury is still out over whether data dumping will lead to increased or decreased revenue for ransomware gangs.
“Whether the 'steal then encrypt' business model proves to be more profitable than traditional encryption-only attacks remains to be seen," Emsisoft's Callow says. "Will companies really be willing to pay criminal enterprises for a pinky promise not to release or monetize their data if a ransom is paid? Or not to extort them a second or third time? Also, the fact that companies may notice the exfiltration occurring and take action prior to ransomware being deployed means there could be fewer successful attacks."
Coveware believes that ransomware gangs' data-dumping strategy is doomed to fail, for two reasons.
First, once the data has exited the building, the smart move is to unleash the corporate attorneys and have them notify regulators, since the data will have already been exposed to malicious actors. In other words, it's a data breach. As Coveware notes: "It's not the crime, but the coverup" that causes real trouble.
"The negative press from the breach can only become worse if the negative press includes a coverup," it says. "This being said, we don’t expect all victims to self-disclose. Some will choose to pay and mitigate potential brand damage."
Second, attackers' data-leaking threats and follow-through attempts to shame companies into paying may backfire. "Shame can evoke anger and obstinance as a response, not obedience and control as the attackers hope," Coveware says. "Additionally, companies facing this threat can mitigate the effects by taking the responsible, high road - notify law enforcement, make the required notifications and disclosures, vow to make security amends - and can even win applause by stating they won't give in to cyber extortion by paying."
Many experts continue to emphasize that paying ransoms - especially now in response to data leak threats - encourages future attacks. "Proactive measures, strong monitoring and a clear policy of not paying is imperative," McAfee's Samani tells ISMG. "We have to ensure that this business model fails."
'Unfortunate Realities'
As the data breach notification boilerplate so often states: "Cyberattacks are one of the unfortunate realities of doing business today." Even well-prepared businesses can fall victim to data breaches or ransomware. But as Maersk and Norsk Hydro have demonstrated, communicating clearly about what has happened, remaining transparent and working to improve defenses buys enormous goodwill.
So often, in other words, it's less about organizations getting hacked, and more about how they respond to the hack. Even so, prepare for a flood of dumped data as ransomware gangs keep testing to see if "naming and shaming" will indeed drive more victims to pay a ransom.